Password managers as one of the security steps
What do you use the Internet for? It allows some to keep up to date with the latest news. For some, it is a one-stop-shop for shopping, games, and job search. For some, it is a tool for connecting with friends and family, both when they are away from home and when they are close to it. But more important is how you use the Internet. Young people are much more inclined to engage in risky behavior online and in such interactions – to be deceived and lose money. Use complex, unique passwords for different accounts. We often choose passwords that are easy to remember, such as names or birthdays. But just as they are easy for you to remember, so are they easy for cybercriminals to guess. If you use the same, simple password for multiple accounts, cybercriminals can – and certainly will – access all of your sensitive personal information.
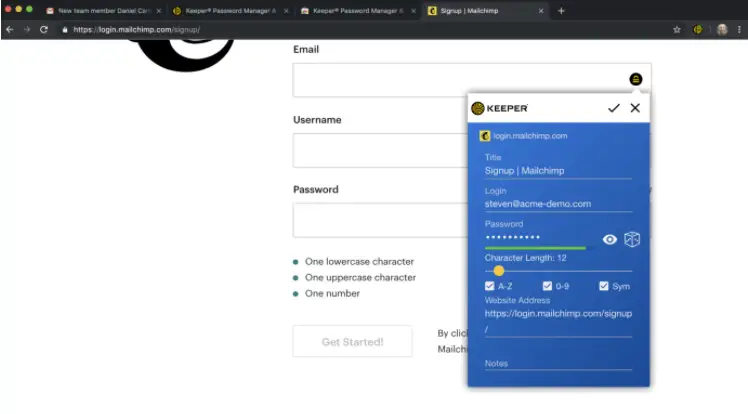
Use the password manager to securely store multiple passwords in different accounts and make sure each password is complex; with at least 10 characters and a mixture of numbers, letters, capital letters, and special characters.
For the user, this is the most convenient solution because passwords are used not only on desktop computers but also on smartphones and tablets. In this case, you only need to enter your login and master password to start the synchronization. All codes are at your fingertips anytime, anywhere. However, such services require you to trust the vendor and ensure that the master password is not available to him and that there is no way to access the database in any other way.

Password managers as one of the security steps
Using the program is very simple – first, the user enters one password for the application, and she, in turn, puts them wherever she can according to the data entered by the user. Storage can contain not only passwords but also full-fledged accounts. We can say that this application is very fast. There is a separate service for electronic payment, which is very important because the transfer of money via the Internet has become an integral part of our daily lives. There is also a function for generating passwords.
Download password managers, it’s very easy. Besides, they have several basic functions. Some password managers are designed to quickly create a password if you do not want or do not have time to come up with a complicated password using a unique combination of letters, symbols, and numbers that an ordinary person cannot pick up or a program that can analyze this type of combination. This type of program is the simplest and is built, to a large extent, on the principles that so-called random number generators work with.
Do not accept contacts with strangers on social media
Many of the people you meet online are not what they claim to be. It is common for cybercriminals to create fake social media profiles to encourage relationships with careless users and try to rob them – and maybe worse.
If an unknown person contacts you online and insists that you share personal information or give them money, this should be an alarm signal. If possible, check the person to see if their account is authentic. Still unsure of that person’s identity, but still want to accept their friendship request? To be sure, restrict the data that is visible on your profile using privacy settings. Remember: the identical rules apply online as within the world – don’t share sensitive or personal information with strangers.
Do not accept contacts with strangers on social media
Protect sensitive and personal information
With a few exceptions, unfortunately, there is no button to permanently delete content you have posted online. Any picture, comment, or photo you post online will probably stay there forever. Even if you remove the original post, you can’t be sure that others haven’t already copied or shared your content on other networks. Therefore, do not put anything on the Internet that you do not want others to see.

Protect sensitive and personal information
A tried and tested tactic of cybercrime is to trick you into downloading malware that allows them to steal your information. From a popular game to an email offering technical support, malware can be disguised in many different ways.
Avoid downloading apps that look weird or are on an unfamiliar website. Not sure if the email you received is well-intentioned? Ask yourself the following questions: Does the sender have a strange email address? Is the greeting generic? Are there a lot of spelling mistakes? Is there a strange sense of urgency?
If you are still unsure, get in touch with the brand or company through official channels, such as a website or social networking site. It is always better to check three times than to risk your safety.
Always use a secure connection
When you use a public Internet connection, such as Wi-Fi in a mall, you have no direct control over the security of the connection. If you cannot establish a secure connection or ensure that your device is protected, do not share sensitive information. It is safer to wait to return home and have a secure Wi-Fi network.
Never rush to click on a link or post. There is nothing more urgent than our online security. Avoiding online threats can be stressful, but there are many resources to help you. Whenever you find yourself in a situation where you are unsure or suspicious, rely on the expertise of those you trust – friends, parents, teachers, or even a technology partner.
If you don’t update the protection, cybercriminals will come up with a way to break it in someday. Systematically monitor operating system updates and check privacy settings on the applications and browser you use. Stay safe and secure, don’t be lazy, and take risks. Listen to tips and use secure applications.

